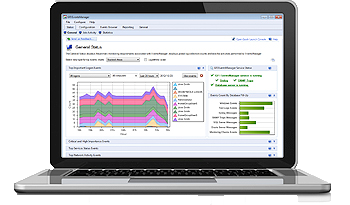
Effective security strategies not only include real-time monitoring of log data. Regular analysis of security-relevant event logs is also essential. This is the only way to identify critical incidents, suspicious activities, and threat trends in time to take immediate countermeasures. Monitor policies, access controls (e.g., authentication and authorization), activities (including users with elevated privileges), and applications (IDS, IPS, firewalls, etc.) that are critical to the security of your network-in real time.
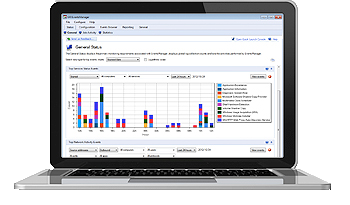
System failures happen. At best, they are only slightly noticeable. Or at the other extreme, they can have severe consequences. Be prepared: Monitor the availability, health, performance and utilization of all your IT assets-whether network devices, workstations, servers, applications, business and infrastructure services or network protocols.
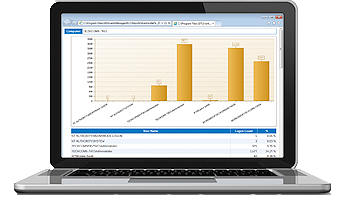
Institutional security standards and legal requirements for data security predominantly demand that all important log data is captured, consolidated, managed and stored in a tamper-proof manner. Companies need to be able to provide a traceable record of activity in their IT environment. GFI EventsManager ensures reliable, secure log data collection, analysis and consolidation, supported by forensic analysis, two-factor authentication and compliance reporting.
Other benefits:
- More reliable protection Optimize protection measures - security incidents detected and assessed by log analysis help you do this.
- Improve productivity Reduce costs and make your IT department more productive by automating IT management.
- Easier Compliance Meet regulatory and institutional compliance requirements (SOX, PCI DSS, HIPAA, FISMA, etc.) more easily.
- Reduce downtime Automatically detect, investigate and resolve incidents with active network and server monitoring and log data.
alphared cybersecurity GmbH & Co. KG
Breslauer Straße 49
04299 Leipzig (Germany)
Fon: +49 (0) 341 / 860 70 80
Fax: +49 (0) 32 12 / 104 30 74
Mail: info@alphared-cybersecurity.com


